When you visit a web site, your request and the response data are sent
as a series of packets, each consisting of a header containing
addressing and sequencing information, and a payload or data section
in which the information resides. Packets are typically relatively
small (less than
![]() bytes). In order to analyze the
traffic and detect attacks, one needs to collect the packets, and may
need to process either the header or the payload. We will (somewhat
arbitrarily) denote an attack that can be detected by investigating
the header only a ''network attack'' while leaving those that
require investigation of the payload in the ''host attack'' realm.
bytes). In order to analyze the
traffic and detect attacks, one needs to collect the packets, and may
need to process either the header or the payload. We will (somewhat
arbitrarily) denote an attack that can be detected by investigating
the header only a ''network attack'' while leaving those that
require investigation of the payload in the ''host attack'' realm.
One reason for this distinction is encryption. If the data are encrypted (for example, data from a secure web site), the header remains in the clear, and so this information is still available for analysis by the statistician. The payload is inaccessible (assuming a sufficiently strong encryption scheme) and so cannot be used to detect attacks until it is decrypted at the destination host. For this reason (and others), we consider any attack that requires investigation of the data in a packet to be better detected at the host than on the network.
There are several protocols used on the Internet to ensure a level of performance or reliability in the communication. We will briefly discuss TCP (the Transmission Control Protocol), since it is one of the most important ones, and will allow us to discuss a class of denial of service attacks. For more information about the various protocols, see ([32]).
First, however, it is necessary that we discuss the Internet Protocol
(IP).
This protocol is not reliable, in the sense that there is no mechanism
in place to ensure that packets are received. The IP header contains
the source and destination IP addresses, which are ![]() -bit integers
identifying the sending and receiving computer for the packet. There
are other fields in the packet that are used to control the routing of
the packet, et cetera, but we will not dwell on these here. As always,
interested readers should investigate ([32]) or any of
the many books on the TCP/IP protocol suite.
-bit integers
identifying the sending and receiving computer for the packet. There
are other fields in the packet that are used to control the routing of
the packet, et cetera, but we will not dwell on these here. As always,
interested readers should investigate ([32]) or any of
the many books on the TCP/IP protocol suite.
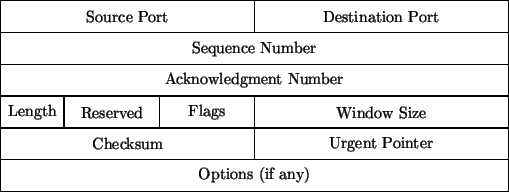
Since IP is unreliable, a packet sent may or may not reach its destination, and if it does not, there is no guarantee that anyone will notice. Thus, a more reliable protocol is required. TCP implements a reliable two way communication channel, and is used for web, email, and many other user applications. The TCP header is shown in Fig. 5.1. The important fields, for this discussion, are the ports, sequence numbers and flags.
The ports are a method for identifying a specific session, and can be
thought of as a ![]() -bit addition to the IP address that uniquely
determines the session. Ports are also used to identify the
application requested. For example, port
-bit addition to the IP address that uniquely
determines the session. Ports are also used to identify the
application requested. For example, port ![]() is the standard web
port, and web browsers know that in order to obtain a web page from
a server they need to make a connection on this port.
is the standard web
port, and web browsers know that in order to obtain a web page from
a server they need to make a connection on this port.
To initiate and maintain a connection, the flags and sequence numbers are used. The TCP protocol requires a three-way handshake to initiate a connection. First the client sends a SYN packet (in this manner we will denote a packet with only the SYN flag set; similarly with other flag combinations) to the server. The server responds with a SYN/ACK packet, acknowledging the connection. The client then finalizes the connection with an ACK packet. Sequence numbers are also passed, and tracked to ensure that all sent packets are received and acknowledged, and to allow the reconstruction of the session in the correct order. Packets that are not acknowledged are resent, to ensure that they are ultimately received and processed.
 |
Once a session has been instantiated through the three-way handshake, packets are acknowledged with packets in which the ACK flag is set. In this manner the protocol can determine which packets have been received and which need to be resent. If a packet has not been acknowledged within a given time, the packet is resent, and this can happen several times before the system determines that something has gone wrong and the session is dropped (usually by sending a reset (RST) packet). Note that this means that if there is no response to the SYN/ACK packet acknowledging the initiation of the session there will be a period (of several seconds) in which the session is kept open by the destination host as it tries resending the SYN/ACK hoping for a response. This is the basis of some denial of service attacks, which we will discuss in the next section.