
Next: 10. Interactive and Dynamic
Up: csahtml
Previous: 9.7 Privacy and Security
-
- 1
-
Adam, N. and Wortmann, J. (1989). Security-Control Methods for Statistical
Databases: A Comparative Study. ACM Computing Surveys, 21(4):515-556.
- 2
-
Agrawal, R. and Srikant, R. (2000). Privacy-preserving Data Mining. In
Proceedings of the ACM SIGMOD International Conference on Management
of Data,
pp. 439-450.
- 3
-
Bauer, A. and Günzel, H. (eds) (2001). Data Warehouse
Systeme. dpunkt.verlag, Heidelberg.
- 4
-
Bayer, R. (1997). The universal B-Tree for multidimensional Indexing:
General Concepts. In World-Wide Computing and Its Applications `97 (WWCA `97). Tsukuba, Japan, 10-11, Lecture Notes on Computer
Science, Springer Verlag.
- 5
-
Bayer, R. and McCreight, E. (1972). Organization and maintenance of large
ordered indexes. Acta Informatica, 1(3):173-189.
- 6
-
Beckmann, N., Kriegel, H.-P., Schneider, R. and Seeger, B. (1990). The
R
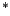 -tree: An efficient and robust access method for points and rectangles.
In Proceedings of the ACM SIGMOD International Conference on Management of Data, pp. 323-331, New York.
-tree: An efficient and robust access method for points and rectangles.
In Proceedings of the ACM SIGMOD International Conference on Management of Data, pp. 323-331, New York.
- 7
-
Chan, C.-Y. and Ionanidis, Y.E. (1998). Bitmap index design and evaluation.
In Proceedings of the ACM SIGMOD International Conference on
Management of Data, pp. 355-366.
- 8
-
Chin, F.Y. and Özsoyoglu, G. (1982). Auditing and inference control in
statistical databases. IEEE Transactions on Software Engineering, 8(6):574-582.
- 9
-
Comer, D. (1979). The ubiquitous B-Tree. ACM Computing Surveys, 11(2):121-138.
- 10
-
Cox, L.H. (1980). Suppression methodology and statistical disclosure
control. Journal of the American Statistical Association, 75:377-385.
- 11
-
Denning, D.E. (1982). Cryptography and Data Security. Addison-Wesley.
- 12
-
Dobkin, D., Jones, A.K. and Lipton, R.J. (1979). Secure databases:
Protection against user influence. ACM Transactions on Database Systems, 4(1):97-106.
- 13
-
Domingo-Ferrer, J., Oganian, A. and Torra, V. (2002). Information-Theoretic
Disclosure Risk Measures in Statistical Disclosure Control of Tabular Data.
In Proceedings of the 14th International Conference on Scientific and Statistical Database Management (SSDBM '02).
- 14
-
Duncan, G. and Keller-McNulty, S. (2001). Disclosure risk vs. data utility:
The R-U confidentiality map. Technical Report. Statistical Sciences Group. Los Alamos National Laboratory.
- 15
-
Dzeroski, S. and Lavrac, N. (eds) (2001). Relational Data Mining, Springer Verlag, Heidelberg.
- 16
-
Elmasri, R. and Navathe, S.B. (1999). Fundamentals of Database Systems, 3rd Edition, Addison Wesley.
- 17
-
Fellegi, I.P. (1972). On the question of statistical confidentiality.
Journal of the American Statistical Association, 67(337):7-18.
- 18
-
Fellegi, I.P. and Sunter, A.B. (1969). A Theory of Record Linkage. Journal of the American Statistical Association, 40,
1183-1210.
- 19
-
Gaede, V. and Günther, O. (1998). Multidimensional Access Methods. ACM
Computing Surveys, 30(2):170-231.
- 20
-
Gray, J., Bosworth, A., Layman, A. and Pirahesh, H. (1996). Data Cube:
A Relational Aggregation Operator Generalizing Group-By, Cross-Tab, and
Sub-Total. In Proceedings of the 12th International Conference on Data
Engineering (ICDE'96), New Orleans, USA, IEEE Computer Society, pp. 29-53.
- 21
-
Gupta, H., Harinarayan, V., Rajaraman, A.J. and Ullman, D. (1997). Index
selection for OLAP. In Proceedings of the Thirteenth International Conference on Data Engineering (ICDE '97), Birmingham U.K., IEEE Computer Society.
- 22
-
Guttman, A. (1984). R-trees: A dynamic index structure for spatial
searching. In Proceedings of the ACM SIGMOD International Conference on Management of Data, pp. 47-57.
- 23
-
Huyn, N. (1997). Multiple-view self-maintenance in data warehousing
environments. In Proceedings of the 23rd Conference on Very Large Databases (VLDB), pp. 26-35.
- 24
-
IBM (2003). DB2 OLAP Server.
http://www-3.ibm.com/software/data/db2/db2olap/library.html
- 25
-
Inmon, W.H. (1992). Building the Data Warehouse, Wiley, New York.
- 26
-
Jarke, M. Lenzerini, M. Vassiliou, Y. and Vassiliadis, P. (2003).
Fundamentals of Data Warehouses, 2nd ed., Springer, Berlin et al.
- 27
-
Jürgens, M. (2002). Index Structures for Data Warehouses. Springer Lecture Notes in Computer Science,
Berlin/Heidelberg/New York.
- 28
-
Kimball, R. (1996). The Data Warehouse Toolkit. Wiley, New York.
- 29
-
Lechtenbörger, J. and Vossen, G. (2001). Quality-oriented Data Warehouse
Schema Design. In information technology, vol. 45, 190-195.
- 30
-
Lehner, W., Albrecht, J. and Wedekind, H. (1998). Normal Forms for
Multidimensional Databases. In Proceedings of the 10th International Conference on Scientific and Statistical Data Management (SSDBM'98), Capri, Italia, 63-72.
- 31
-
Lenz, H.-J. (1994). A rigorous treatment of Microdata, Macrodata and
Metadata. In Dutter, R. (ed.), Proceedings in Computational
Statistics, Physica, Heidelberg.
- 32
-
Lenz, H.-J. and Shoshani, A. (1997). Summarizability in OLAP and Statistical
Databases, In Proceedings of the 10th International Conference on
Scientific and Statistical Data Management (SSDBM'97), Washington, USA.
- 33
-
Lenz, H.-J. and Thalheim, B. (2001). OLAP Databases and Aggregation
Functions. In Proceedings of the 14th International Conference on
Scientific and Statistical Data Management (SSDBM'01), Washington, USA.
- 34
-
Li, Y., Wang, L., Wang, X. and Jajodia, S. (2002). Auditing interval-based
inference. In Proceedings of the 14th Conference on Advanced
Information Systems Engineering (CAiSE'02), Toronto, Canada.
- 35
-
McCarthy, J. (1982). Metadata Management for Large Statistical Databases, In
Proceedings of the 8th International Conference on Very Large Data Bases, Mexico City, Mexico.
- 36
-
Messerschmidt, H. and Schweinsberg, K. (2003). OLAP mit dem SQL-Server, dpunkt. verlag, Heidelberg.
- 37
-
Microsoft (1998). OLE DB for OLAP Programmer's Reference.
- 38
-
Microsoft (2003). Microsoft SQL Server: Data Transformation Services (DTS).
http://www.microsoft.com/sql/evaluation/features/datatran.asp
- 39
-
O'Neil, P. and Quass, D. (1997). Improved query performance with variant
indexes. SIGMOD record, 26(2):38-49.
- 40
-
Oracle (2003). Oracle Warehouse Builder - Product Information.
http://otn.oracle.com/products/warehouse/index.html
- 41
-
Neiling, M. (2003). Identifizierung von Realwelt-Objekten in multiplen Datenbanken. PhD dissertation, Univ. of Cottbus, Germany.
- 42
-
Netscape (1996). Secure Socket Layer 3.0 Specification
http://wp.netscape.com/eng/ssl3/
- 43
-
Raden, N. (1996). Star Schema 101. Archer Decision Sciences, Santa Barbara,
http://members.aol.com/nraden/str101_e.htm (2000.12.12)
- 44
-
Shoshani, A. (1997). OLAP and Statistical Databases: Similarities and
Differences. In Proceedings of the 16th ACM SIGACT-SIGMOD-SIGART Symposium on Principles and Database Systems (PODS'97), Tucson, USA, 185-196.
- 45
-
Spaccapietra, S., Parent, C. and Dupont, Y. (1992). Model independent
assertions for integration of heterogeneous schemas. VLDB Journal, 1(1), 81-126.
- 46
-
Stallings, W. (1999). Cryptography and Network Security, Principles and Practice. Addison Wesley.
- 47
-
Traub, J.F., Yemini, Y. and Wozniakowski H. (1984). The statistical
security of a statistical database. ACM Transactions on Database Systems, 9(4):672-679.
- 48
-
Wirth, N. (1986). Algorithms and data structures, Englewood Cliffs, Prentice Hall.
- 49
-
Wrobel, S. (2001). Inductive Logic Programming for Knowledge Discovery in
Databases. In Dzeroski, S. and Lavrac, N. (eds), Ralational Data Mining, Springer Verlag,
Heidelberg.
- 50
-
Wu, M.-C. and Buchmann, A.P. (1998). Encoded bitmap indexing for data
warehouses. In Proceedings of the 14th International Conference on Data Engineering (ICDE), 220-230.
Subsections